
I get that too. I’ve been an appsec person, developer and product owner at different times.
Clickjacking Cheat Sheet Owasp
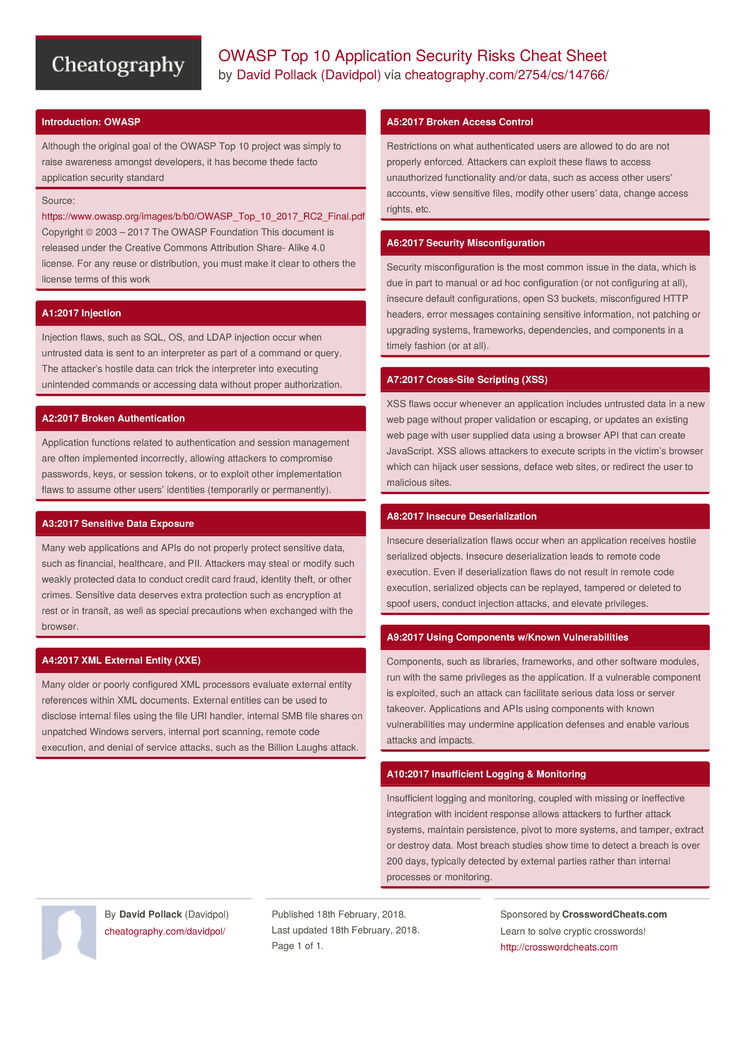
We wanted to create short, simple guidelines that developers could follow to prevent XSS, rather than simply telling developers to build apps that could protect against all the fancy tricks specified in rather complex attack cheat sheet, and so the OWASP Cheat Sheet Series was born. This cheat sheet lists a series of XSS attacks that can be used to bypass certain XSS defensive filters. OWASP. OWASP Proactive Controls: Protect Data Everywhere. OWASP Application Security Verification Standard (V7, 9, 10). OWASP Cheat Sheet: Transport Layer Protection. OWASP Cheat Sheet: User Privacy Protection. OWASP Cheat Sheet: Password and Cryptographic Storage. OWASP Cheat Sheet: HSTS. OWASP Testing Guide: Testing for weak cryptography External. This cheat sheet offers practical tips on five relevant items from the OWASP top 10. Subscribe to the cheat sheet series. When subscribing, you can choose to only receive cheat sheet updates, and nothing else. If you do not want to receive updates and new cheat sheets via email, you can use this direct download link. The OWASP Top 10 is the reference standard for the most critical web application security risks. Adopting the OWASP Top 10 is perhaps the most effective first step towards changing your software development culture focused on producing secure code.
I understand your frustration. Ideally I feel security should be baked in from the beginning with a SDLC process, i.e a friendly security person you can ping/involve from conception through development of a feature. Rather than the all too often 1 week pentest scheduled 1 week before product go live with no time for remediation and no communication with the tester apart from a 20 page report at the end.
Online resource wise, dev security material can be sparse, you either have Troy Hunt or someone else warning you about SSL/TLS configurations (I die on this hill, attackers don’t care if you have a C or A+ SSL labs score because usually that’s nothing to do with how you’re going to get hacked) or XSS (hopefully your framework handles this now) but then nothing really breaking down what request smuggling is and how you can protect against it.


Csrf Cheat Sheet Owasp

Xxe Cheat Sheet Owasp
Owasp Cheat Sheet Series
If you can get a 2 day slot to get a training course in as a dev team with a (decent) security person, that can be really valuable. Gives you enough of a high level overview to get that tingly feeling when maybe something might be a security issue.
